
ACCREDITED BY

The Cyber Excellence Certification scheme is designed to address the growing cybersecurity challenges in the Middle East region. This comprehensive certification provides organizations with the knowledge, skills, and frameworks necessary to build robust cybersecurity capabilities and protect their digital assets.
Our certification scheme is specifically tailored for organizations operating in the Middle East, taking into account regional regulations, cultural considerations, and the unique threat landscape of the region.


The London Strategy Centre (LSC) is the Accreditation Body, holding responsibility for the ownership and maintenance of the certification framework. LSC operates to the highest standards of competence and impartiality. The centre liaises with governments, industry stakeholders, and international partners to align the framework with regulatory requirements and sector-specific needs.
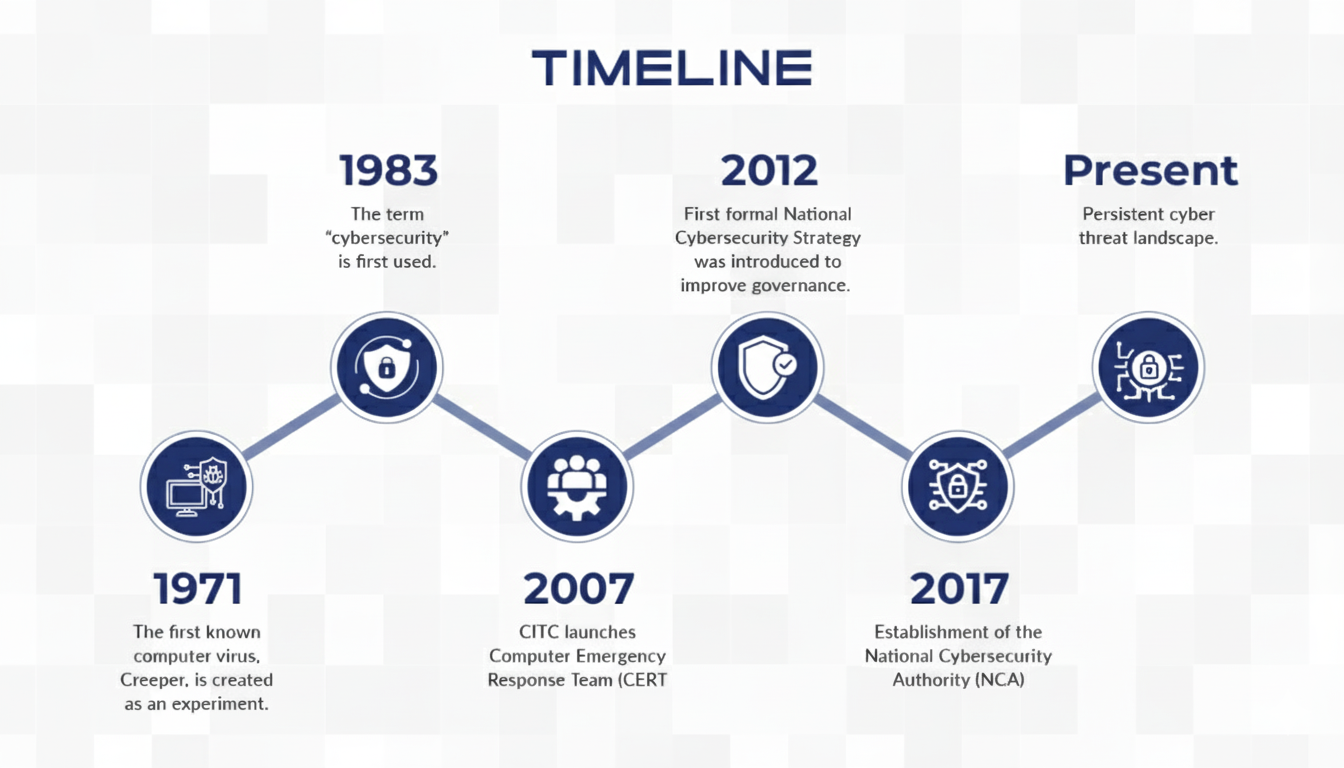
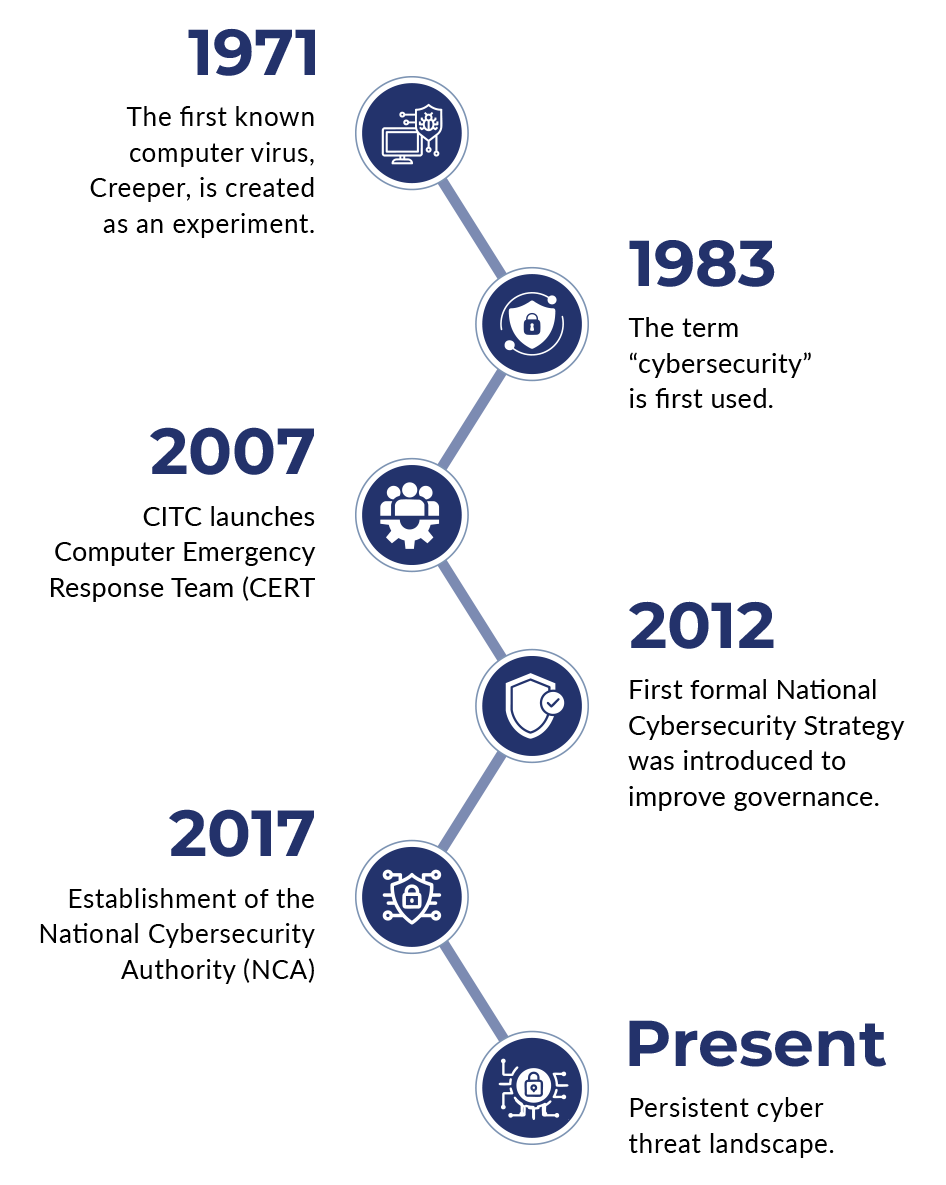
As the Middle East continues to rely more and more on digital platforms, tough cybersecurity measures are not only a business necessity but also a regulatory requirement. The region faces escalating cyber risks that impact organisations across both the public and private sectors. Cyber Excellence was established to address these local challenges, aligning its certification model with regional frameworks such as the Saudi National Cybersecurity Authority (NCA), Essential Cybersecurity Controls (ECC), the UAE Information Assurance Standards (IAS), and the Gulf Cooperation Council (GCC) Cybersecurity Strategy.
By harmonising with these and other national mandates, Cyber Excellence ensures that certification is regionally relevant and internationally credible.

The Middle East faces unique cybersecurity challenges that require specialized solutions. Our Cyber Excellence certification is designed specifically for the region.
Self-assessment for low-risk organisations.

Additional controls for low-risk organisations.

Independent assessment for moderate-risk organisations.

Highest standard for critical infrastructure







We follow the UK's Cyber Assessment Framework (CAF), taking a systematic and comprehensive approach to assessing how effectively the organization responsible is managing cyber risks to essential functions.





of internet-based vulnerabilities mitigated with certified controls.

of certified organisations reported improved confidence in defending against threats.

of buyers prefer certified suppliers.

of organisations see improved executive engagement with cybersecurity.
A leading UK wealth management firm, mandated certification for its partner network. Within a year, this initiative resulted in:

80% reduction in cyber incidents among certified partners

A unified assurance standard across thousands of suppliers.

Simplified compliance via independent certification.
Cyber Excellence adapts these lessons for the Middle East, ensuring both small and large organisations benefit from a cohesive framework.
Cyber Essentials Impact Evaluation (2024), Department for Science, Innovation and Technology (DSIT).

"In cybersecurity, standing still is falling behind. Regular reassessment and updated certification standards create a culture of vigilance, ensuring teams remain aware and proactive. Continuous improvement isn't optional, it's the only way to stay ahead of evolving threats and protect critical assets in an ever-changing digital landscape."
Principal, London Strategy Centre

Self-assessment via a short online questionnaire. Light-touch independent verification of declarations. Scope: Five core technical controls (Cyber Essentials-aligned):
Includes all Level 1 aspects. Independent technical verification by a qualified assessor, including:
Includes all Level 1 & 2 assessment activities.
Includes all Level 1–3 activities.
Cyber Excellence builds on trusted international models like NIST, Cyber Essentials and IASME Cyber Assurance, ensuring globally recognised best practices are applied locally.
Achieving Cyber Excellence certification demonstrates compliance with key client and regulatory requirements ahead of competitors. This strengthens market positioning and opens doors to new business opportunities and high-value contracts.
Cyber Excellence is designed to be accessible to organisations of all sizes, from SMEs to critical infrastructure operators. Its adaptable framework allows businesses to start small and expand their cybersecurity maturity as they grow.
Certification shifts cybersecurity from being an IT issue to a core business priority. By capturing executive attention, it embeds security into everyday decision-making and operational processes.
Cyber Excellence Level 1 is recommended as a minimum standard of cybersecurity that every organisation - no matter its size - should aim for.
To find out more about our certifications or to have a conversation with one of our experts about how we can support you
 www.londonstrategycentre.com
www.londonstrategycentre.com
 London Strategy Centre
London Strategy Centre
 Cyberexcellence@londonstrategycentre.com
Cyberexcellence@londonstrategycentre.com
 45 Albemarle Street, 3rd Floor, Mayfair, W1S 4JL, London, United Kingdom
45 Albemarle Street, 3rd Floor, Mayfair, W1S 4JL, London, United Kingdom

45 Albemarle Street, 3rd Floor,
Mayfair, W1S 4JL, London, United Kingdom
enquiries@londonstrategycentre.com

